Published Jan 05, 2022
How to Mitigate Potential Information Exposures Caused by the Great Resignation of 2021

The summer of 2021 saw record numbers of resignations in the US across sectors. A recent Wall Street Journal article reported over 20 million resignations between April and August 2021. While some industries have inherently gained from this turnover, the sheer number of employees leaving their posts highlights companies’ information security vulnerabilities. With this trend, employees, whether joining or leaving a company, could either purposefully exfiltrate or unintentionally expose critical information.
Lowering the impact of potential exposures
When employees leave en masse, the potential for insider threats and information leaks rises exponentially. Now more than ever, companies need the ability to understand and secure their critical information assets to follow information flows and user sharing behaviors.
Having forensic investigation capabilities within your InfoSec tool kit provides you with invaluable insights into such sharing behavior and information flows to mitigate insider threats and breach attempts.
Gain visibility like never before
Cognni’s forensic features give you unparalleled visibility into information flows and anomalies, user behaviors, highly sensitive information types, and even unauthorized sharing. You can investigate entities at every level and understand if anomalies are truly suspicious, risky, and worth acting upon. At Cognni, entities aren’t just employees, but can be organizations, external contacts, and files themselves because all sorts of actors can be involved in anomalous information behaviors.
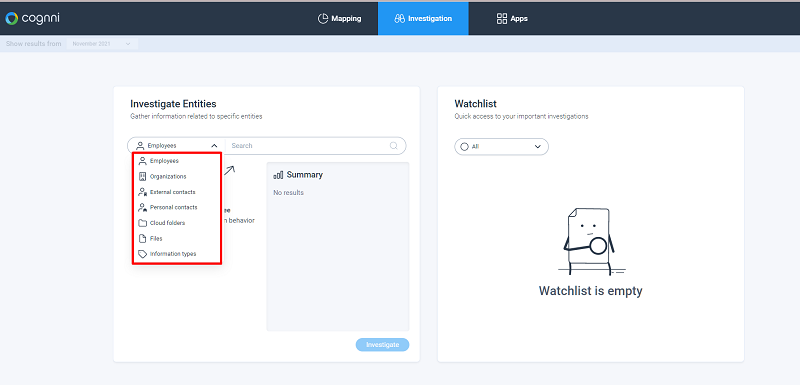
Investigate suspicious user behavior
If an employee or other entity has been found to potentially be jeopardizing your organization – whether by sharing critical information to a private email address, outside the organization, or via an anonymous link – you can run forensics and monitor that employee to get a full picture of their activities and determine appropriate action.
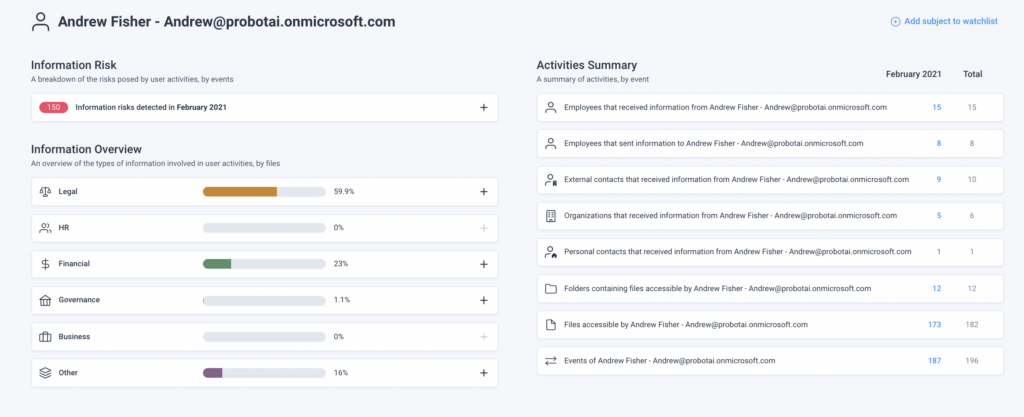
For Example: The Cognni dashboard shows an increase in shares for critical Legal documents. You decide to investigate the situation further and find that your employee, Andrew Fisher, from the HR department, is behind many of these shares.
-
- When you click on Andrew’s profile, you find that he has been sending dozens of documents, including legal contracts and governmental forms, to a private email and to external contacts.
- Because of these actions, you add Andrew to your watch list so that you can easily continue to monitor his sharing behaviors and interaction with critical documents for the coming months.
Monitor employees during their notice period
Cognni’s investigation features can also be used to monitor employees leaving your organization.
For Example: Over the last month both Sarah and Frank have handed in their notices to the Business Development department. Sarah is leaving due to a health issue, but Frank is resigning to join a competing firm.
You are aware that employees who give notice can pose a unique risk to your organization. Some employees may be resigning due to long-time frustrations want to expose your critical information assets for personal gain.
-
- Employees like Frank could be motivated to exfiltrate intellectual property that would benefit their future employee.
- Sarah may act negligently and send important files and projects to their personal email.
Given these scenarios you add Sarah and Frank to your watch list for the duration of their resignation period and ensure that they don’t have access to company accounts after they leave.
Forensic investigation has never been easier
With the Great Resignation exposing new vulnerabilities for major corporations and small businesses alike, properly securing your company’s critical information has never been more important. This requires the ability to track risk and investigate anomalous information flows or user behavior. Cognni’s autonomous intelligence and extensive forensics capabilities allow you to ensure that your critical assets remain in the right hands and set your InfoSec team up for success as they face challenges ahead.
